Table of Contents
Suricata-EVE-Unixsocket
This article provides instructions for installing Suricata-Eve-Unixsocket app in Trisul Network Analytics. The Suricata-Eve app allows you to integrate Suricata IDS alerts into Trisul metrics framework.
Installation
1. Installing Suricata App
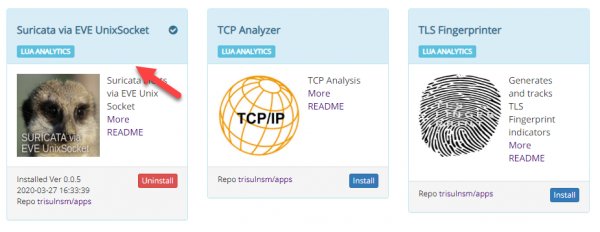
- You can install the app by logging in as admin and selecting Web Admin > Manage > Apps > Suricata via Eve Unixsocket.
2. Installing Suricata version 5.0
Please install Suricata by running the following command,
add-apt-repository ppa:oisf/suricata-stable sudo apt-get update apt-get install suricata
3. Updating with latest ruleset
Use the following command to update the latest emerging-threats ruleset
sudo suricata-update
suricata-update puts the combined rules in /var/lib/suricata/rules which is owned by root. Make sure the trisul user can read this directory.
sudo chown trisul.trisul /var/lib/suricata -R
4. Enabling EVE_unix Socket
- locate the 'Outputs' section in /etc/suricata/suricata.yaml enable EVE logging as shown below.
# Extensible Event Format (nicknamed EVE) event log in JSON format
- eve-log:
enabled: yes
filetype: unix_dgram #regular|
filename: suricata_eve.socket
The Filename is 'suricata_eve.socket' is the name of the Unix Datagram socket file that Trisul will listen to later.
5. Starting Suricata
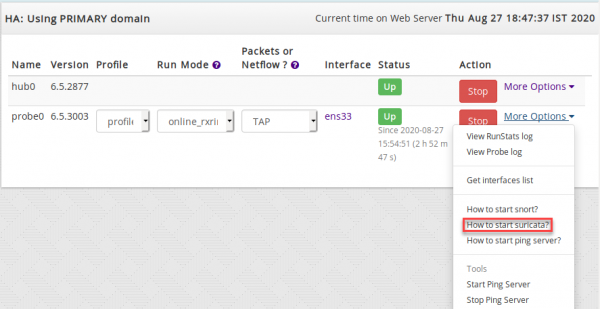
- Login as Admin and Select Admin Tasks.
- Click on 'More options' dropbox at the end of probe0.
- You will find a Dialog box with command line to install Suricata as below.
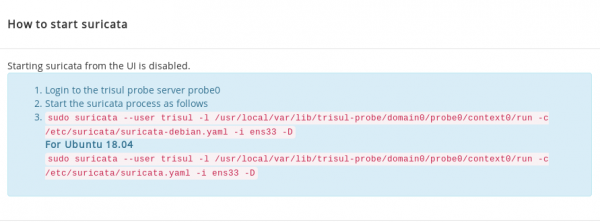
- Cut and paste the command shown into a terminal to start suricata
sudo suricata --user trisul -l /usr/local/var/lib/trisul-probe/domain0/probe0/context0/run -c /etc/suricata/suricata.yaml -i ens33 -D
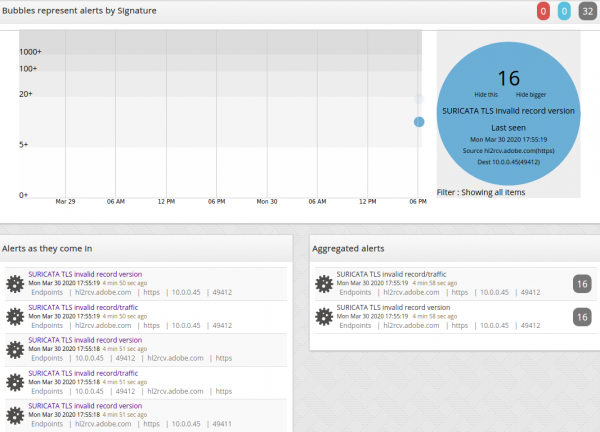
6. Viewing Alerts
7. Starting Suricata Automatically
- You need to install monit to enable this feature.
- Add a shellscript named start-suricata.sh in /usr/local/etc/trisul-probe/
#!/bin/bash echo "Removing PID file" /bin/rm -f /var/run/suricata.pid echo "Starting suricata" /usr/bin/suricata --user trisul -l /usr/local/var/lib/trisul-probe/domain0/probe0/context0/run -c /etc/suricata/suricata.yaml -i ens18 -D echo "Done starting suricata"
- Make sure the shell script start-suricata.sh is executable. It can be done by
chmod +x start-suricata.sh
- You need to add the following statements in the /etc/monit/monitrc file.
check process suricata with pidfile /var/run/suricata.pid start program = "/usr/local/etc/trisul-probe/start-suricata.sh"
- Please ensure you restart monit
systemctl restart monit