Trisul Blog
The first 2024 release of Trisul Network Analytics features enhanced ability to manage Netflow Routers and Interfaces, new Admin tools, and dramatically improved IPDR Compliance flow storage solution.
A fresh new release of Trisul Network Analytics is available for immediate download. Features major performance improvements to provide high volume Netflow ingestion for large ISP applications.
Flow metrics in Trisul Network Analytics measure flow based activity in network rather than bandwidth. This post describes the Top 3 flow metrics that you can put to use today.
Click to read about a major update of Trisul Network Analytics 7.0. What you get is a brand new responsive User Interface, a new compliance mode, and powerful new Netflow analytics features.
Announcing a new release of Trisul Network Analytics with major new features to help you create your own PDF reports, monitor a range of keys for threshold events and improved netflow interface screens.
A new serious remote code execution vulnerability was revealed this week in the logging library Log4J (logging for Java) package. This article explores some options for investigating and detection effects of this vulnerability from the network monitoring side.
Announcing a fresh new release of Trisul Network Analytics with new packages for Ubuntu 20.04LTST(Focal) and Oracle Linux 8 (compatible with RHEL8). This release features enhanced reporting, new utilities and further improvements to Netflow metering. We want Trisul to become the default choice for serious Netflow and Packet traffic analytics teams.
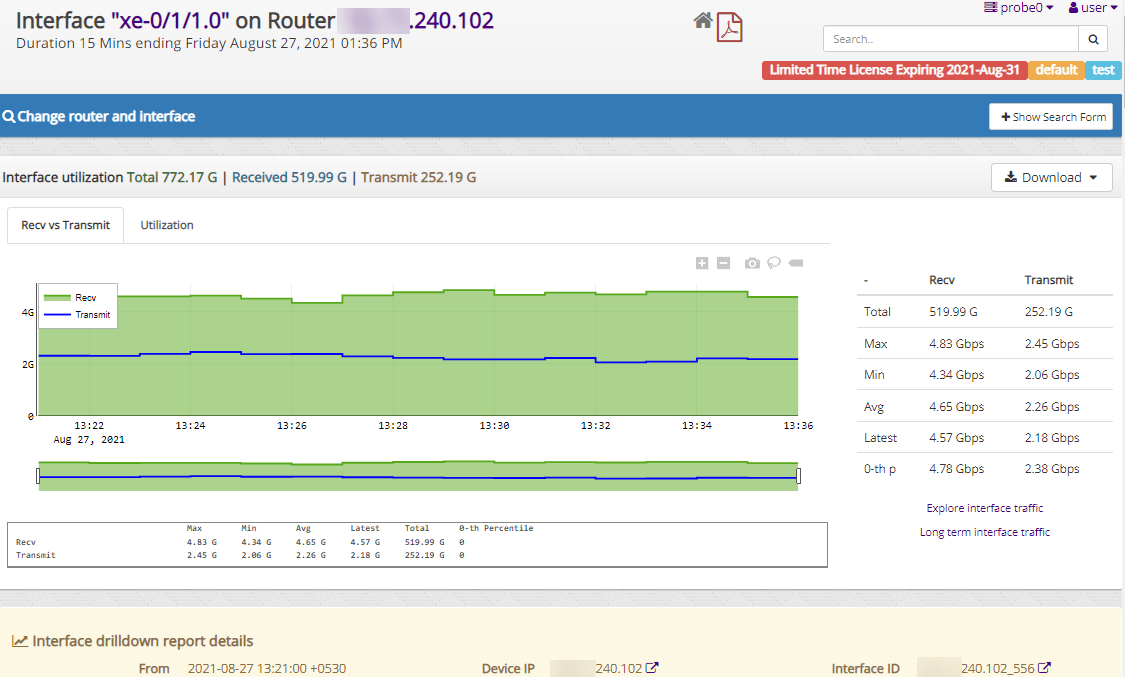
Announcing a new release of Trisul Network Analytics with greatly improved support for Netflow traffic metrics. Improved user interface , stability, and other features are in this important release.
Announcing a new Jan 2021 release of Trisul Network Analytics featuring new Netflow monitoring screens, BGP monitoring for ISPs, and several other features and bug fixes. Free download now.
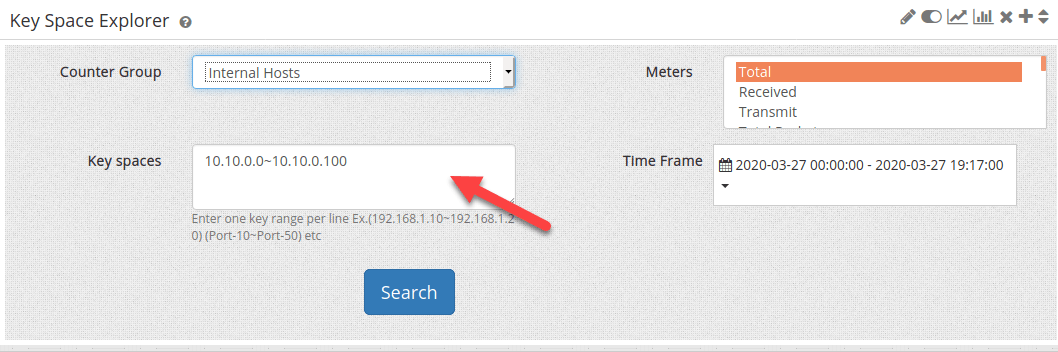
Trisul Network Analytics provides a cool app to monitor activities of IP address ranges.