Table of Contents
Introduction
NetFlow and sFlow have emerged as more effective solutions for network traffic analysis and monitoring. These two powerful technologies can help uncover your network’s blind spots. But what’s the difference between them, and which one is the perfect fit for your organization?
Since NetFlow and sFlow share a common flow-based foundation. Let’s look under the hood of network traffic analysis and examine their intricacies to see how these tools can help you.
Overview of flow telemetry
Before we jump in, first an overview of what these flow measurement technologies are. If you want to check on your network traffic there are volume based and flow based options. In volume-based approach, the network devices (routers, switches) monitor their interfaces, measure the total amount of network traffic, usually in terms of bytes or packets, without considering the specific characteristics of individual flows and report to a management system, and trigger alerts when traffic exceeds certain thresholds. SNMP is the technology used to accomplish this. Limitations of SNMP include the inability to distinguish between types of traffic like video streaming or file type, might not detect subtle changes in traffic patterns that makes it challenging to identify potential threats.
Whereas a flow-based approach provides a more nuanced and detailed understanding of network traffic. Here, the network device tracks packets, updates flow records, exports them to a collector, and analyzes the data to gain insights into network traffic. Hence network admins gain improved visibility including who is talking to whom, what protocols are being used, and how much bandwidth is being consumed. It helps them to quickly identify and troubleshoot issues, help detect potential threats, and plan capacity upgrades.
Most of today’s routers, firewalls, switches support both volume based (SNMP) and flow based measurement support. NetFlow and SFlow are the two flow-based measurement techniques. They are also referred to as Flow Telemetry in various technical literature.
Let’s look at NetFlow and SFlow.
What is NetFlow
NetFlow, a widely adopted network protocol developed by Cisco collects and exports IP traffic information. Almost all of todays vendors support NetFlow often under their own trademark names like JFlow, NetStream, CFlowd etc.
NetFlow enables detailed network traffic analysis by creating flow records for packets by means of a flow table, tracking Layer 3 and Layer 4 headers, and exporting this data to a collector for analysis. This allows administrators to gain insights into network traffic patterns, optimize routing and switching, and ensure Quality of Service (QoS) for critical applications.
Versions: Lets take a look at the NetFlow versions predominantly used in 2024 including v5, v9, and IPFIX.
NetFlow v5
- Released in 2000
- Supports IPv4 and IPv6
- Limited scalability and flexibility
NetFlow v9
- Released in 2004
- Template-based, allowing for flexible and customizable data export
- Supports IPv4 and IPv6
- Improved scalability and performance
IPFIX (Internet Protocol Flow Information Export)
- Released in 2008 (RFC 5101)
- An IETF-standardized protocol based on NetFlow v9
- Provides improved scalability, flexibility, and interoperability
- Supports IPv4 and IPv6
What is sFlow
sFlow is a network protocol developed by InMon Corporation that gives you the lowdown on your traffic. It’s commonly used for traffic analysis, security monitoring, and capacity planning.
So, how does it work? sFlow uses random packet sampling at configurable rates to create flow records based on Layers 2-4. Then, it exports that data to a collector for analysis. This helps admins understand network traffic patterns, fine tune network resource allocation, and detect anomalies.
Difference between NetFlow and sFlow
| NetFlow | sFlow | |
| Sampling Method | Typically uses a caching-based approach, where every packet is analyzed and cached. | Employs a statistical sampling method, where packets are randomly selected for analysis. |
| Sampling Rate | Typically samples every packet (1:1 ratio). | Samples packets at a configurable rate (e.g., 1:100, 1:1000). |
| Flow Creation | Creates a new flow record for every unique combination of source/destination IP addresses, ports, and protocols. A flow cache is maintained. | Creates a new flow record based on every sampled packet. There is no flow or connection tracking. |
| Flow Export | Exports flow records at regular intervals (e.g., every 5 minutes). | Exports flow records as soon as they are created. |
| Scalability | Can become resource-intensive on high-speed networks. | Built for high-speed networks and large-scale deployments. |
| Accuracy | Provides detailed, accurate information about network traffic. | Offers statistical accuracy, with a trade-off between accuracy and scalability. |
| Encrichment | Flow records can be enriched with data from Network Address Translation (NAT), BGP Routing, Application Detection (NBAR) and so on | No enrichment |
| Port | Default port is UDP 2055 | Default port is UDP 6343 |
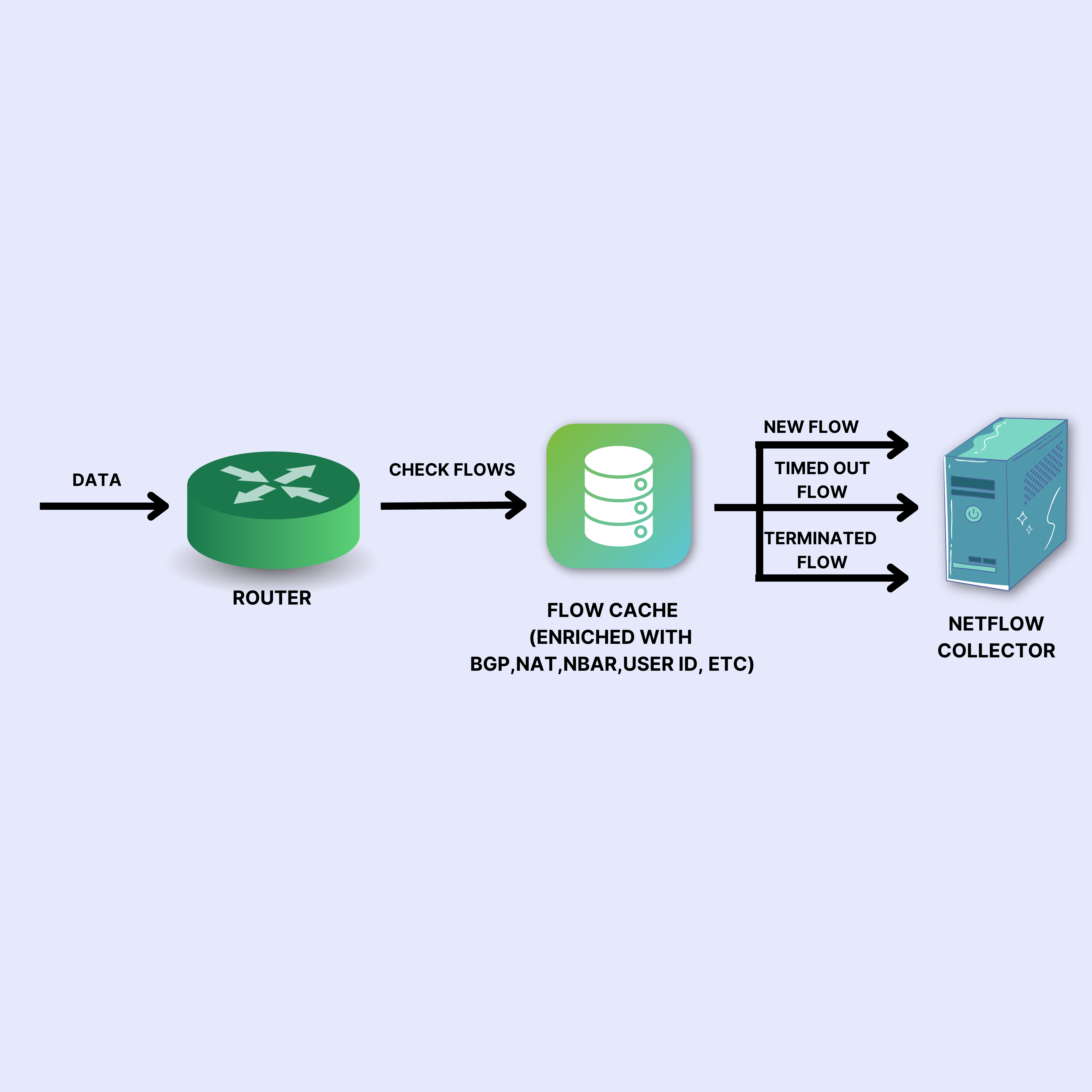
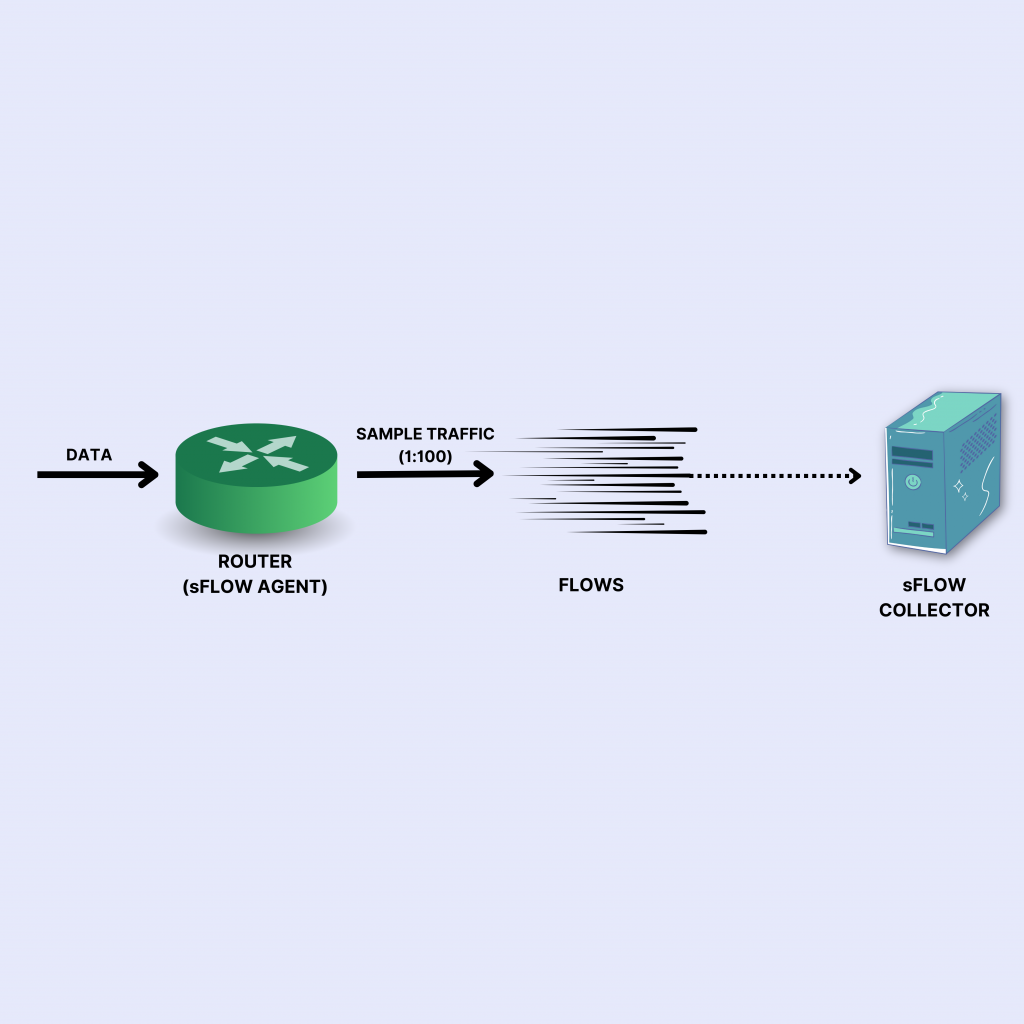
Deeper under the hood
Let’s take a look at what SFlow and NetFlow packets looks like on the wire.
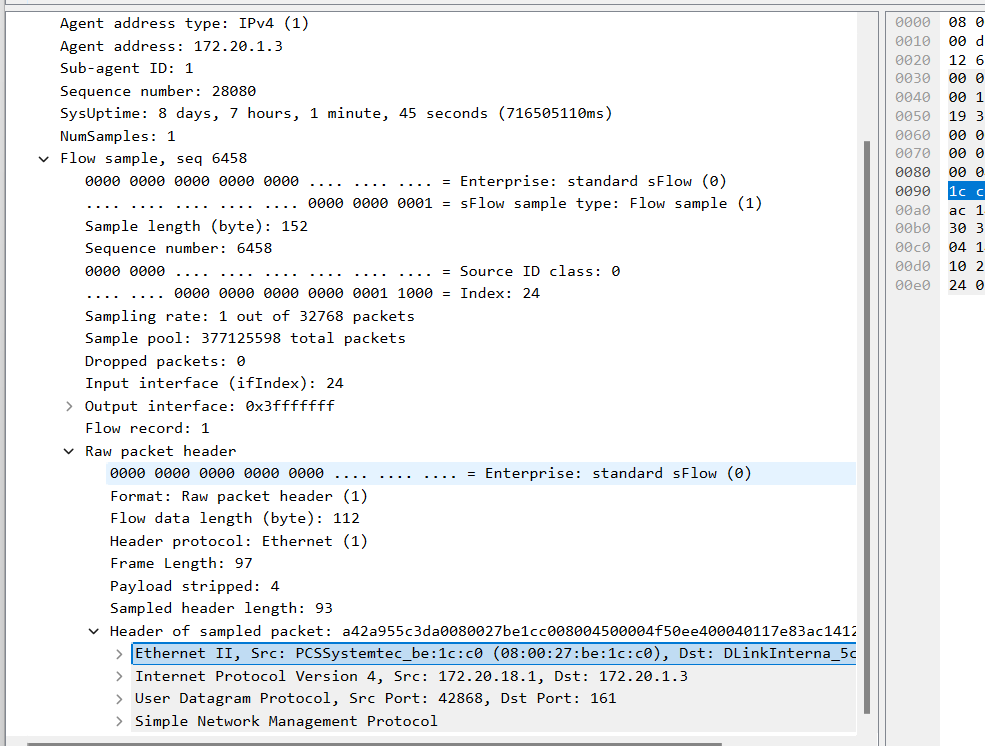
On the left side you have the NetFlow packet decoded using Wireshark. On the right side you can see the SFlow decode.
You can notice the following.
In addition to the flow fields such as source/dest IP, source/dest Port, Protocol, ingress and egress intefaces – the NetFlow decode contains fields taken from the NAT module, the NBAR module, the UserID integration, BGP routing table (Source/Dest AS which arent shown). The NetFlow processor on the device enriches the flow record with these fields taken from other components of the router or firewall.
Now observe the SFlow decode on the right side. The information is simply the header of the sampled packet. You can see that the flow contains merely the raw bytes from the packet starting from the link layer Ethernet header upto 64 bytes. The receiver has to construct the flow from the sampled packet header. The upside is it includes the MAC (Layer II) information as well.
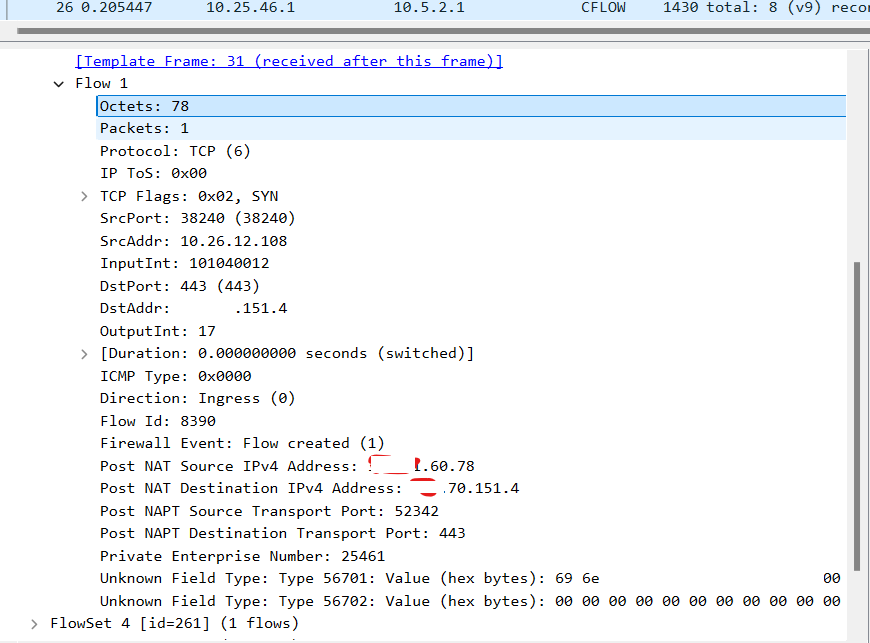
As you can see the NetFlow packet in this case taken from a PaloAlto firewall is
- Far more comprehensive
- Flexible because it uses Templates to add fields. Templates are information packets that define what information is included in the actual flow packet.
- You can see fields like
Post NAT IP Address. NetFlow can enrich flows with NAT, BGP, NBAR, UserID, and other information - Aware of connection state , you can see fields like
Duration
The SFlow packet decode taken from an entry level DLink Switch is
- Simple just includes the header bytes from the actual sampled packet
- Maintains no state – just grabs every 1000th (sample rate) packet and send it across
- Requires very little resources
- No way to get NAT, BGP, or any other information
- SFlow can include interface counters. However this is rarely used in practice because the preferred way to get interface counters is via SNMP.
Choosing between NetFlow and sFlow
Consider the following factors:
- Network Size and Complexity: sFlow might be more suitable for large, high-speed networks, while NetFlow might be better for smaller, more complex networks.
- Accuracy Requirements: If you need detailed, accurate information about network traffic, NetFlow might be the better choice. For statistical accuracy and scalability, sFlow might be more suitable.
- Resource Constraints: If your network devices have limited resources, sFlow’s sampling-based approach might be more suitable.
Trisul NetFlow Analyzer
Trisul NetFlow Analyzer supports both NetFlow and SFlow. With SFlow you gain Layer 2 MAC counters by default. With NetFlow all enrichments are supported such as User-ID, App-ID, NBAR, NAT Translations, BGP AS , Prefix, Next Hop information and so on.
Conclusion
Network administrators can gain improved visibility into network traffic using flow-based approaches like NetFlow and sFlow. While both technologies offer valuable insights, the key differences lie in their sampling methods, scalability, and accuracy.
NetFlow: Ideal for smaller, complex networks requiring detailed traffic information.
sFlow: Suitable for large, high-speed networks where statistical accuracy and scalability are crucial.
Ultimately, the choice between NetFlow and sFlow depends on your organization’s specific needs, network size, and complexity.
TRY OUR SOLUTION NOW AND