Trisul Blog
Announcing a new Oct 2024 release of Trisul Network Analytics, with tons of new features, improved documentation, and easy new configuration. Get started with an enhanced 7-day free trial. No credit card required.
Explore the importance of advanced bandwidth monitoring and top reasons to choose Trisul NetFlow Analyzer over traditional monitoring in today's scenario.
Anomaly detection plays a key role in ensuring modern network safety; here's how we've researched and implemented deep learning technologies to improve our algorithms.
Investing in a NetFlow Analyzer is essential for ensuring operational excellence and enhancing your company's ROI. Take a look at the comprehensive guide.
Discover how Trisul NetFlow Analyzer revolutionizes network traffic analytics with streaming analytics, machine learning, and advanced features for efficient, strategic network management.
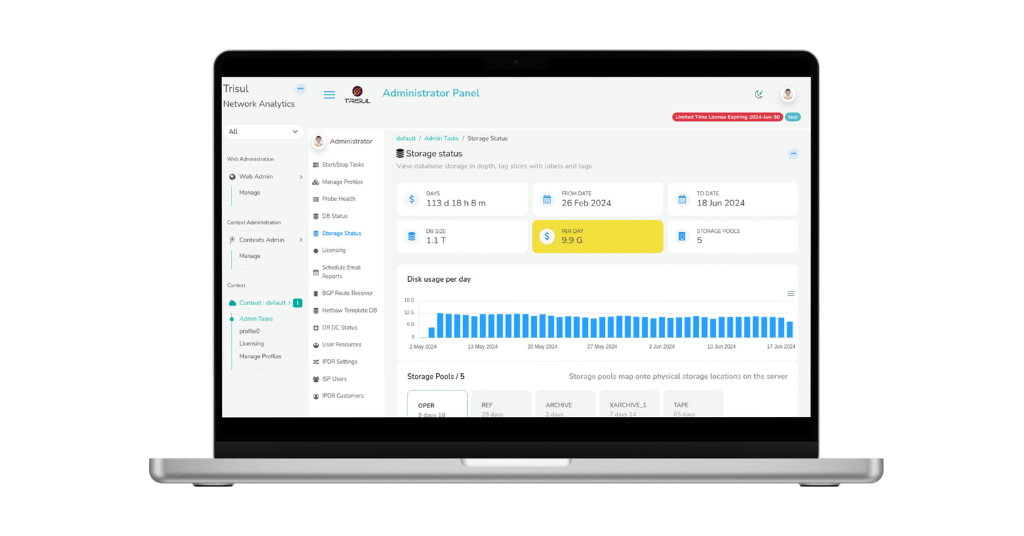
Discover the latest Trisul Network Analytics release, version 7.0.3167! This update features a new Storage Analyzer, faster IPDR compliance, and upgraded NetFlow Analyzer with improved reporting and FortiGate integration. Update now or Sign Up at Trisul.org.
The primary use case of IPDR Logging is for regulatory compliance. IPDR plays a significant role in ensuring data privacy and protection by capturing and storing only the essential network flow parameters required for compliance.
Internet Protocol Detail Record (IPDR) is a standardized format for ISPs to gain a comprehensive insight to enhance their network management and ensure regulatory compliance and audit.
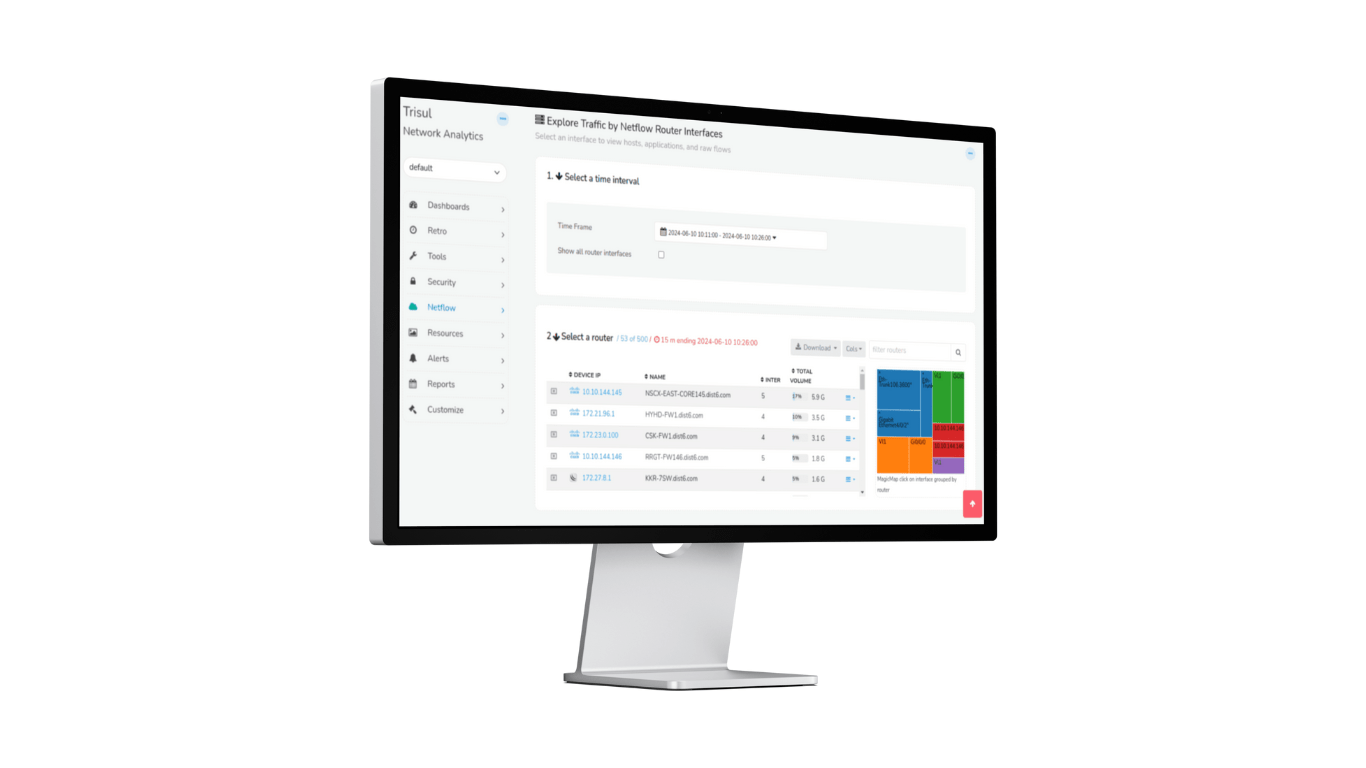
The first 2024 release of Trisul Network Analytics features enhanced ability to manage Netflow Routers and Interfaces, new Admin tools, and dramatically improved IPDR Compliance flow storage solution.
A fresh new release of Trisul Network Analytics is available for immediate download. Features major performance improvements to provide high volume Netflow ingestion for large ISP applications.