Trisul Blog
A new March 2020 release of Trisul Network Analytics is available with new distributed tooling, feature updates, and bug fixes.
We are thrilled to announce the launch of our new Trisul Network Analytics website
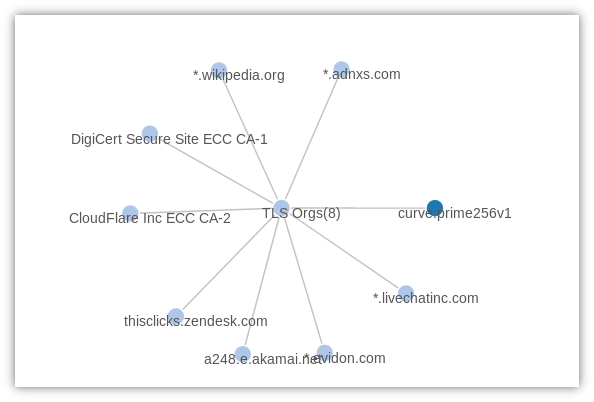
CVE-2020-0601 describes a vulnerability that exists in the way Windows CryptoAPI (Crypt32.dll)validates Elliptic Curve Cryptography (ECC) certificates.
One of the hardsells in Network Security Monitoring is to convince a user that storing packet trails is a feasible proposition.
Happy New Year Trisul fans. We have a new release out for you with some Enterprise features.
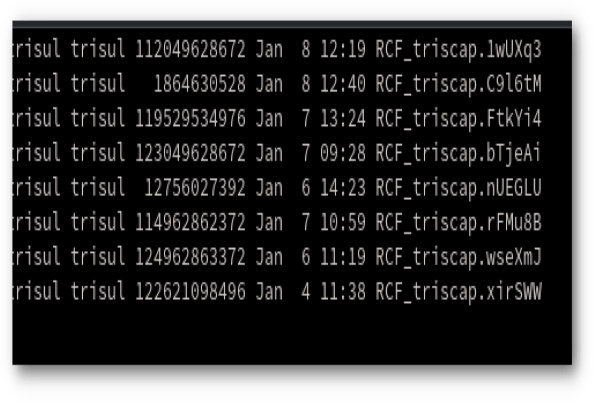
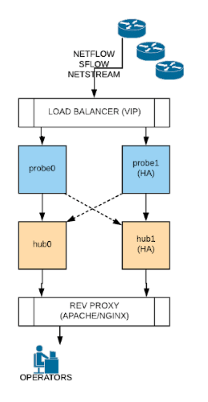
We have a new release out for you with some Enterprise features. HA : High availability – protects against a single probe or hub node failure by multihoming the nodes.
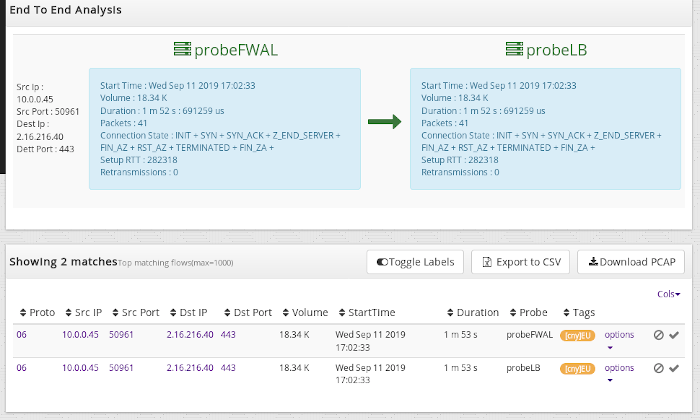
We just pushed a new release of Trisul Network Analytics which will greatly enhance your network troubleshooting capabilities
We are pleased to announced a new release of Trisul Network Analytics. Some highlights of this release. (full release notes)
We are pleased to announced a new release of Trisul Network Analytics. Some highlights of this release. (full release notes)
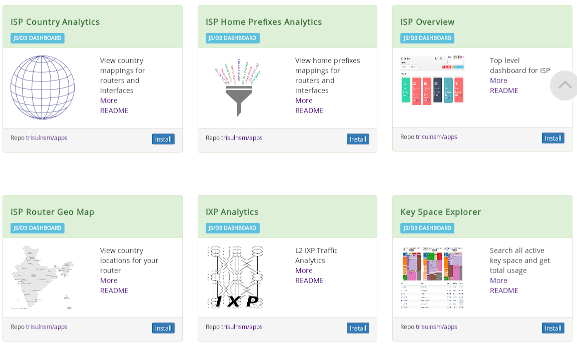
A partial list of the most important features. Trisul APPS are free extensions for real time analytics and visualization