Table of Contents
Introduction
In the age of disruptive technology, network administrators face an uphill battle in ensuring network security, optimizing performance, and troubleshooting issues. To stay ahead of the curve, it’s essential to gain comprehensive network visibility. One crucial metric that offers unparalleled insights is User ID.
Alternative methods of gaining network visibility rely on IP addresses, but this approach falls short compared to User ID-based visibility. Here is why! IP address-based approaches are limited to device-level visibility only, lacking the context of individual users. This limitation makes troubleshooting time-consuming and challenging, as network admins are left without crucial user context. Furthermore, IP-based approaches struggle to meet compliance requirements due to inadequate user tracking, leaving organizations vulnerable to regulatory risks.
In this blog, we’ll explore how Palo Alto empowers NetFlow Analyzer to achieve accurate network visibility.
Limitations with IP Address based Analysis
While IP address-based NetFlow Traffic Analysis is a widely adopted approach, User ID-based analysis offers efficiency, particularly in edge cases like shared IP addresses, remote or mobile users, complex VLANs and subnetting, and BYOD environments. The limitations of IP address-based analysis become apparent when dealing with dynamic IP addresses, which can change frequently. Furthermore, IP addresses can be easily accessed within a specific VLAN and location, making it challenging to accurately identify individual users, especially when they change locations. In such scenarios, User ID-based NTA provides a more reliable and accurate solution, offering unparalleled visibility into user activity.
What is User ID
Palo Alto Network’s next-gen firewalls utilize User-ID attributes a flow to an actual user. This approach differs from traditional IP address-based tracking, as User-ID remains consistent even when IP addresses change. By using User-ID information from logs, network administrators can gain enhanced visibility, establish user-level privilege access, and facilitate forensic investigations into security incidents with detailed user activity information.
How does the User ID work
Palo Alto firewalls can extract the User-ID information by means of an agent installed on Windows Domain Controllers, Exchange Servers and others. The Palo Alto User-ID Agent within the Domain Controller processes these authorization and IP Address assignment logs and forwards them to the firewall. The agent in the firewall generates a corresponding table. Upon the user’s connection attempt, the firewall’s agent verifies the table and policy. Based on the policy, the agent either permits or denies the connection. Finally, when exporting NetFlow records the Firewall adds the User-ID information per flow.
Benefits of User ID
Enhanced Visibility
User ID provides network administrators with detailed visibility into individual user activity, regardless of location or IP address. This enables them to track user behavior, detect potential security threats, and optimize network performance.
Improved Security
By utilizing User ID, network administrators can implement user- and group-based policy control. This is achieved by configuring user-based mapping and group-based mapping, integrating them with IP addresses. As a result, security is enhanced through more precise access control and threat detection.
Improved Logging
User ID facilitates more accurate and detailed logging of user activity. By incorporating User ID into log data, network admins can gain a more comprehensive understanding of user behavior.
Reporting
With User ID, network admins can generate more informative and granular reports on user activity. These reports provide valuable insights into user behavior, helping administrators optimize network resources, detect security threats, and refine their policies.
Improved Forensics Analysis
By providing detailed information on user activity, User ID facilitates the investigation process, allowing administrators to quickly identify the source of security breaches and take safety measures.
Integrating Palo Alto with Trisul NetFlow Analyzer
When you select NetFlow Analyzer during the first login “Selecting the Product Mode” – User-ID and App-ID for Palo Alto is automatically enabled. There is nothing special to be done to gain access to User-ID.
The following monitoring is automatically added, we are sharing some screenshots below for illustration.
- Users choking network ports: Drill down on any interface to find out which users are using the most traffic.
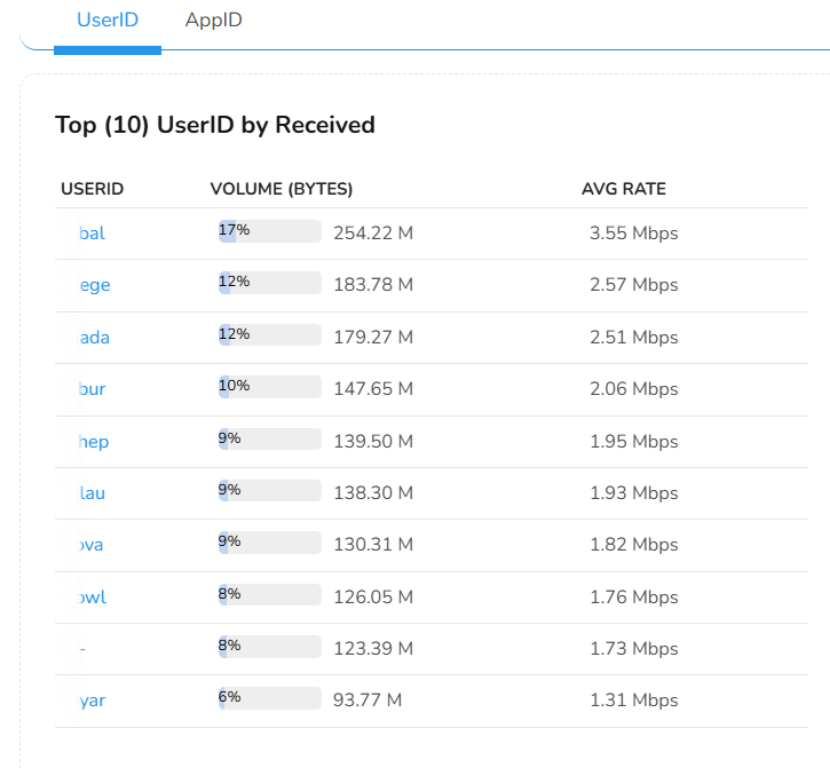
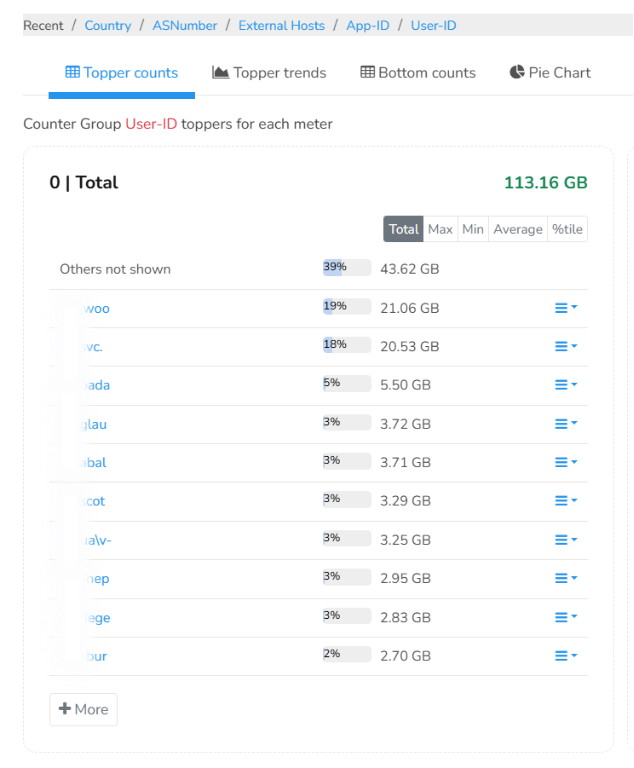
- Top Talkers: Overall Top User-ID transmit and receive. This maps to actual users across the enterprise downloading and uploading the most data, creating the most number of flows
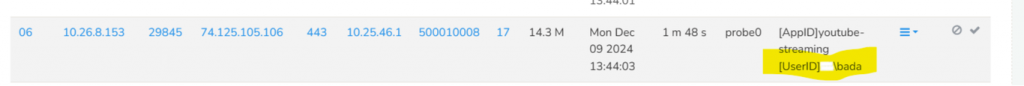
- Explore Flows: Using Trisul Automatic Flow Taggers , a User-ID is tagged on a per-flow basis allowing you to instantly identity the user.
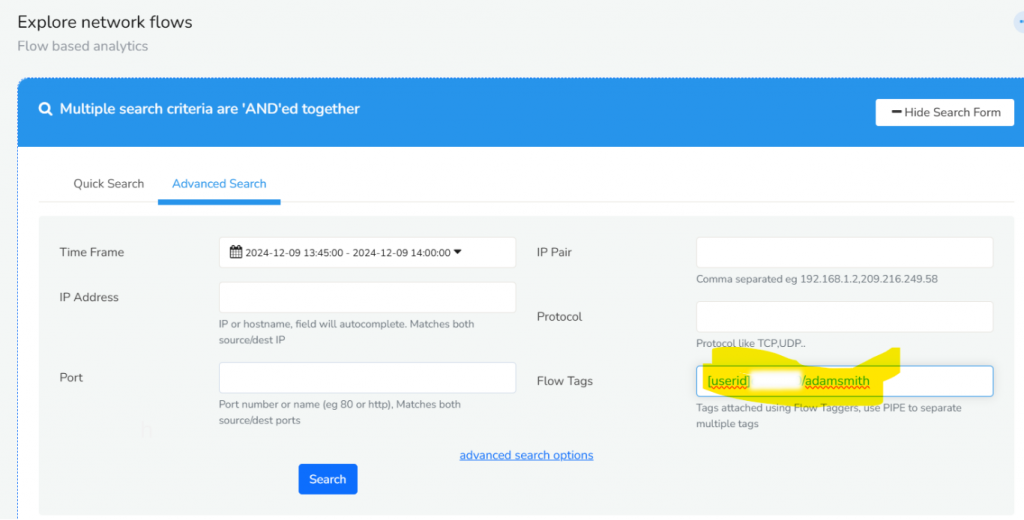
- Search flows by User-ID: Using the [userid]USERNAME format you can use the Explore Flows tool to pull up all flows for a specific user.
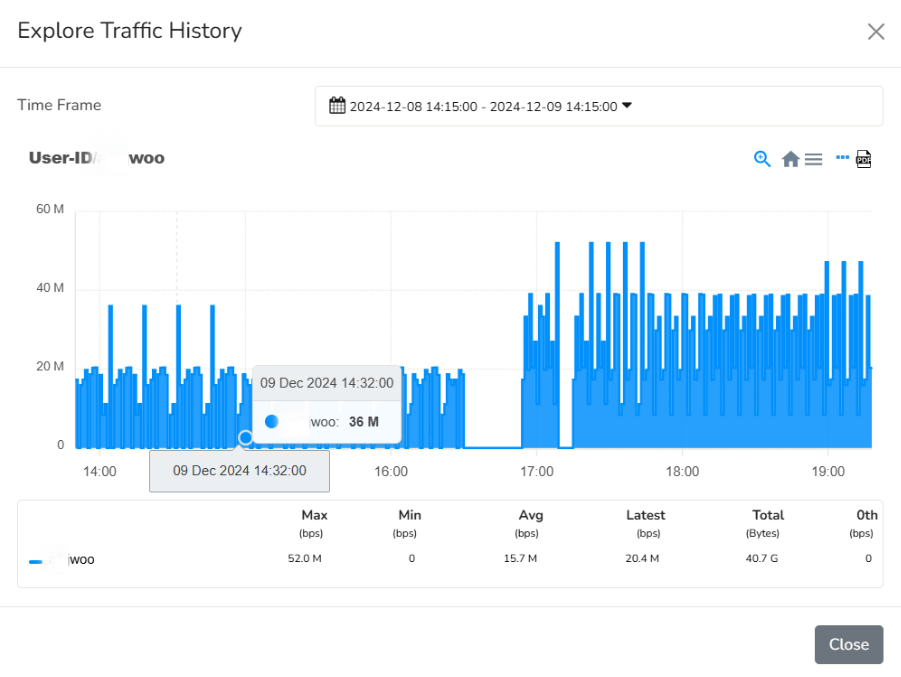
- Traffic charts: You can plot the traffic chart of every user.
Conclusion
In conclusion, achieving accurate network visibility is crucial for network admins to ensure network security, optimize performance, and troubleshoot issues. By leveraging User ID and integrating Palo Alto with NetFlow Analyzers like Trisul, admins can gain unparalleled insights into user activity, enhance security, and improve logging and reporting capabilities. This powerful combination enables enhanced network monitoring, threat detection and improved compliance.
References:
- Palo Alto Networks User-ID page https://www.paloaltonetworks.com.au/technologies/user-id
STOP STRUGGLING WITH NETWORK BLIND SPOTS
