New Feature Spotlight: How Audit Log helps you integrate Trisul security events with SIEM
As we continue our series on the new features of our latest release, let’s turn the spotlight on one of the highly anticipated features developed by Trisul- “The Audit Log”.
So, in this blog, we’ll pick apart the functionalities of the audit log, their importance, and
how enterprises benefit by integrating the audit log with SIEM.
Trisul Audit Log allows you to see the most important events from a security perspective. Typically you send Trisul Audit Logs to a SIEM system to keep track of login attempts, failed logins, changes to configuration and so on.
Introduction
In this modern era of emerging threats, ensuring the security, integrity , and compliance of enterprise systems is critical. Audit logs serve as a key component in this endeavor by tracking and recording critical events. We’ll see all the event types Trisul covers in this release in detail later in this blog.
To start with, let’s scratch the surface of audit logs to understand it better. Actions that are performed in your system or data in the system create an audit trail. But where do you go to see that trail?
An audit log is a comprehensive record of all changes in the web server user activity occurring within an organization’s system. They are aggregated logs of events in chronological order providing valuable insights into the system activity that allows enterprises to track user behavior, resources consumption, and detect potential security threats.
So, What’s Cooking in Audit Logs?
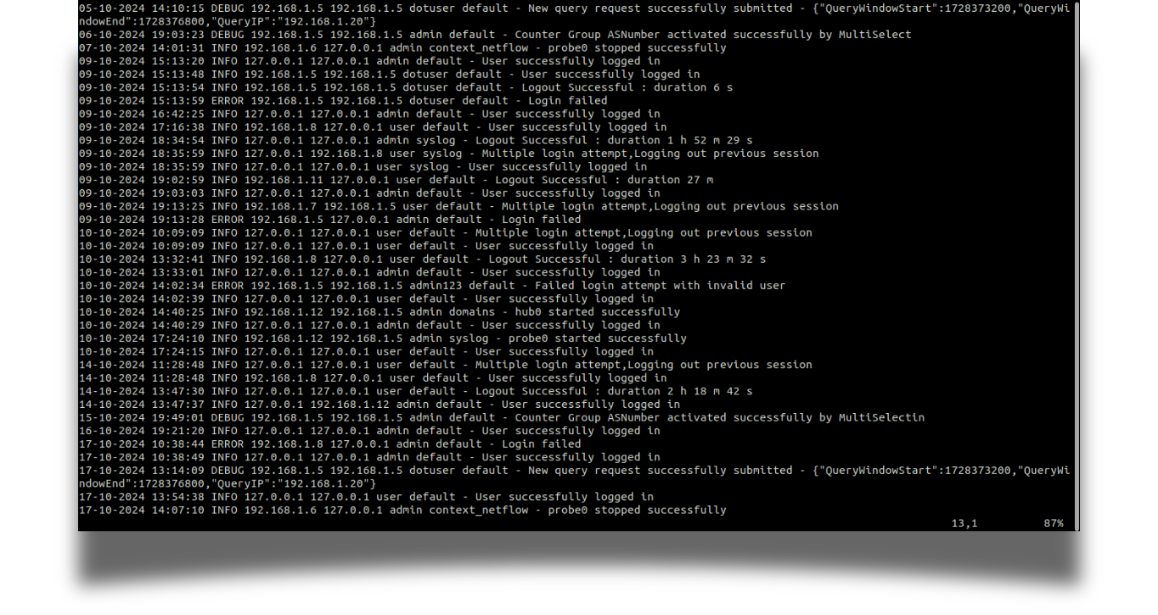
Your audit log is where you go to see the detailed trails of the changes in your system including the timestamp of the logged event, event severity classification, and original IP address of the client such as a computer or mobile device that initiated the request (it identifies where the request truly came from), the IP address of the proxy server that forwarded the request on behalf of the client (when the request passes through the proxy, the server receiving the request sees the proxy’s address instead of the client’s original one), username who triggered the event, instance in which the event occurred, and a descriptive message on the logged activity.
Sample: 19-09-2024 18:39:14 INFO 192.168.1.20 127.0.0.1 user default – User successfully logged in
| Name | Sample Value | Description |
| Time Stamp | 19-09-2024 18:39:14 | The timestamp of the logged event. |
| Severity Level | INFO | Event severity classification (example, INFO, WARNING, ERROR) |
| HTTP Real IP | 192.168.1.20 | Original IP address of the client that retrieves the value from the HTTP header. |
| Request IP | 127.0.0.1 | IP address of the proxy server requested by the client. |
| Username | user | Username who triggered the event. |
| Context Name | default | Instance in which the event occurred. |
| Log Message | User successfully logged in | A descriptive message on the logged activity. |
With these specifications, the web server user activity logs in the audit log records the
start/stops, changing of databases, modifying users and permissions, and so on. Let’s
see them in detail.
- Hub start/stop: Records the start and stop the event of the hub
- Successful login/logout: Tracks successful user logins and logouts
- Invalid username/password: Logs failed login attempts due to incorrect
credentials - Multiple logins: Detects and records multiple simultaneous logins by the same
user - Users add/delete: Tracks changes to user accounts like user added or user
deleted - Password change: Records password changes
- Password reset: Logs passwords reset events
- Counter group: Tracks changes to counter groups including creating, deleting,
enabling, and disabling - IPDR query: Logs IPDR queries
- Report generation: Records report generation events
- Disabled user login: Tracks login attempts by disabled users
- Forceful logout: Logs forced logouts including admin-initiated
- User cross-context login: Records if a user attempts login from a different
tenant/instance.
Benefits
These aggregated logs help security analysts to find who initiated the event, when was
the event initiated, the duration of the event, and prioritize the event based on the
severity level. They are invaluable for organizations to keep the deployment secured
and compliant.
Integration with SIEM
Now that you know what’s cooking in your audit log and its benefits, Let’s see how enterprises integrate audit logs with Security Information and Event Management (SIEM) systems like Splunk, ELK Stack, or IBM QRadar, etc and take it to the next level. SIEM is a unified console for security and incident management that feeds on aggregated logs that enhance threat detection, compliance management, incident response, and security analytics.
For more check out the Audit Log documentation
Final Thoughts
In today’s complex threat landscape, audit logs are a vital layer of defense. By
understanding the functionalities and benefits of audit logs, enterprises can ensure the
security, integrity, and compliance of their systems.