Trisul’s High Security Feature for Unmatched Platform Protection: The Iron Clad Security You Need in 2025
In today’s digital landscape, security has evolved from a defensive mechanism to a fundamental requirement. At Trisul, we understand the importance of fortifying your Trisul server against potential threats. With our latest release, we’re taking our dedication to security to the next level. This is the outcome of a long and deep VAPT exercise we undertook over the past few months with our top security conscious customers.
With Trisul’s high security feature you can proactively secure your Trisul server against the most advanced threats before they can be exploited. This feature serves as the backbone of our security framework, rendering your network virtually bulletproof against threats.
Here’s a rundown of the common vulnerabilities our new feature protects your system against.
XSS Attacks: Blocked and Logged
Wikipedia cites that in the second half of 2007, XSSed documented 11,253 site-specific cross-site scripting vulnerabilities, whereas Symantec reported 2,134 traditional vulnerabilities during the same timeframe. Consequently, cross-site scripting (XSS) attacks that involve injecting malicious code into websites to steal user data or spread malware have become a prevalent threat. However, Trisul’s high security feature effectively counters them. When an XSS attack is detected, the feature logs the offending word and redirects the user to an error page ensuring that your system remains safe.
SQL Injection: A Thing of the Past
With Trisul’s high security feature, SQL injection attacks which exploit vulnerabilities using malicious SQL code are effectively neutralized. Upon detecting suspicious SQL syntax, our feature automatically blocks and logs the attempt redirecting users to a secure error page. This proactive defense mechanism ensures your database remains secure safeguarding your system against potential breaches and data compromises.
Error Handling: Securing Sensitive Information
Trisul’s enhanced error handling mechanism has been designed with security in mind. When errors occur, our system carefully conceals sensitive details such as socket paths and specific code errors preventing them from being exposed on error pages. This ensures that your system’s confidential information remains protected even in the face of unexpected errors.

Server Information Protection
With Trisul’s high security feature enabled, your server’s identity remains concealed from potential hackers. The server name in HTTP responses is masked, preventing attackers from gathering crucial information about your system. This adds an extra layer of security, making it more difficult for attackers to exploit vulnerabilities.
Strict Password Policies: A New Standard
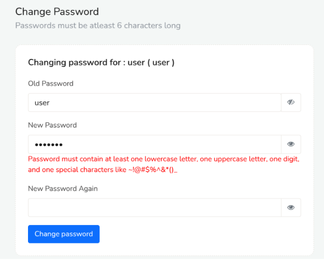
We’ve raised the bar on password security with our new strict password policies. Passwords must now contain:
- More than 6 words
- At least one capital letter
- At least one small letter
- At least one number
- At least one special character
The minimum character length can also be adjusted using Web Trisul options.
Credentials Protection: No More Saved Passwords
When Trisul’s high security feature is enabled, credentials are not saved for the login page. This means that even if a user returns to the login page their credentials will not be auto-filled adding an extra layer of security to your system.
At Trisul, we’re committed to providing you with the best possible security features. Our latest release is a testament to our commitment to security, with a robust feature designed to protect your system from a slew of vulnerabilities. With Trisul, you can rest assured that your system is protected by a fortress of security.
Strict String Validation in High-Security Mode: What You Need to Know
Trisul’s High-Security feature introduces rigorous input validation to prevent potential SQL and JavaScript injection attacks. This includes:
- String inputs for hostnames, custom keys, usernames, and descriptions are scrutinized for suspicious patterns. If any input contains strings that resemble SQL or JavaScript injection attacks, it will be discarded.
- In NetFlow mode, interface names and aliases are also subject to this validation. If any alias or name matches known SQL or JavaScript injection attack patterns, it will not be stored or displayed.
This enhanced input validation provides an additional layer of security, ensuring that your system remains protected from malicious input.
How to enable High Security Mode
To enable High Security Mode and take advantage of its robust security features, refer to the Trisul documentation: How to Enable Trisul High Security Feature