Table of Contents
Enabling Ingress and Egress Netflow - issues and valid use cases
A packet belonging to a IP flow enters a device at an ingress interface and exits through an egress interface. Many routers today have an option to enable Netflow at the ingress interface or at the egress interface or at both. This technical note describes the issues with the options.
Netflow has historically been an ingress only technology. Later versions of Netflow added the option to enable netflow at the egress interface as well. One way wonder how an analyst can get both the interfaces if Netflow is enabled in one direction only. The answer lies in the structure of the Netflow record. Every Netflow record contains both the ingress and egress interface numbers.
Enabling both ingress and egress can result in inconsistent data
Enabling both ingress and egress netflow using on Cisco
ip flow ingress
ip flow egress
will result in a netflow record being generated once at the ingress interface and once again at the egress interface. As noted earlier,both these records contain the same input and output interface details. Hence, this can cause inconsistent or double counting at the netflow receiver.
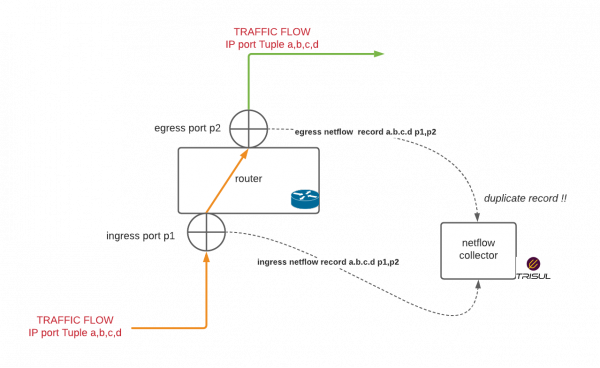
Example : Ingress and Egress enabled on both downstream and upstream interfaces
The following diagram shows both ingress and egress enabled on downstream interface p1 and upstream p2. A packet that flows through p1 will get a netflow record shown by the dotted line labelled ingress netflow and again exiting through p2 will get another netflow record shown by the dotted line egress netflow.
This can
- Result in double counting
- If used with a sampler can cause inconsistent data
When to use ingress and egress netflow
In our customers there are valid use cases for enabling both ingress and egress netflow. The thumb rule is when you have a router that has clear division between upstream interfaces and downstream interfaces you can enable ingress + egress on the upstreams only
In some ISP environments, there can be hundreds of downstream interfaces/sub interfaces that correspond to customers. Enabling netflow on these small and dynamic interfaces can be a chore. The upstreams however will be a handful.
The rules to enable both ingress and egress on the upstreams are:
- Upstream interfaces should not route traffic between themselves (double counting)
- Downstream interfaces should not route traffic between themselves (missing traffic)
- Downstreams should only exchange with upstreams and vice versa
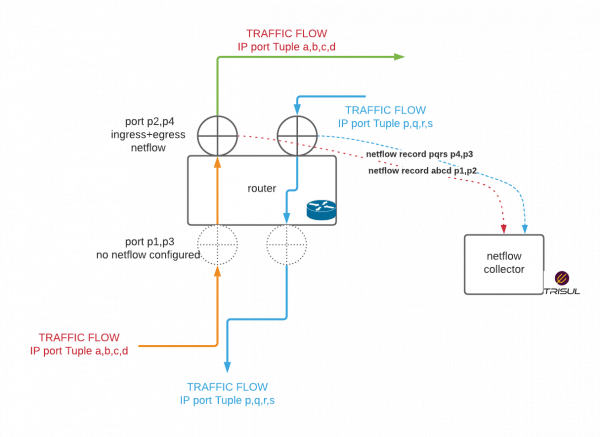
The following diagram shows a valid use case.
In this example the red and blue flows are measured for Netflow at the upstream interfaces only. Hence there will be no duplicate or inconsistent data.
Performance note about egress netflow
In addition , please check with your vendor if there are any performance implications for enabling egress netflow. Cisco has issued the following note 1)
Egress NetFlow accounting might adversely affect network performance because of the additional accounting-related computation that occurs in the traffic-forwarding path of the router.
Configuration options in Trisul
The following are relevant Netflow configuration parameters in Trisul Network Analytics.
IgnoreV9EgressFromDevices: A list of device IP addresses. Egress direction netflows will be ignored from these devicesIgnoreAllEgress: Ignore egress netflow from all devices.
Trisul automatically detects duplicate flow records which arrive within a time window and removes them.