Table of Contents
TLS Fingerprinter
TLS Fingerprinting is a technique by which you can identify SSL/TLS clients. We have launched a new Trisul App that adds this capability to TrisulNSM. This page discusses this new App.
What is TLS Fingerprinting
This technique builds upon the patterns found in the preferences that are advertised in the “Client Hello” message that is sent by the client as the very first message in the TLS Handshake process. This message is unencrypted, so it allows for NSM tools like Trisul to look at it. Every SSL/TLS Client uses a particular version of a particular implementation of SSL/TLS library. Some major implementations are OpenSSL, GnuTLS, Windows, Java SSE, NSS, WolfSSL etc.
The 3 major fields in the Client Hello that can identify a client are
- Ciphersuite : A ciphersuite is a combination of the Key Exchange+Encryption. The list of ciphersuites and the preferences usually change per implementation and by version. A few clients specifically prefer certain ciphersuites. For example Chrome is increasingly in favour of ChaCha20-Poly1305. Most other apps such as malware may just use the defaults that the library provides.
- Extensions : Which TLS extensions are supported and in what order are they seen in the message. This depends on the SSL library type and version. Some advanced clients like Chrome dynamically use extensions to check for SPDY support for example.
- Elliptical Curves: There are about 25 Elliptical Curve types registered by IANA. This number and preference will also vary by client.
So if you take all the three together there is a high likelyhood that you can minimize collisions and identify a particular client on a particular operating system.If you printed out the values of all these three fields and then computed a MD5 hash over the string, we can get a 'fingerprint'. We can call this a JA3 hash as proposed by the researchers John Althouse and team.
At first, this approach may seem a bit flaky but it is not easy for an application to change its print dynamically without some major code rewrite. We currently have about 300 hashes largely due to Lee Brotherston's effort. We at Trisul also added in some 50-60 new prints.
- Lee Brotherstons work on TLS Fingerprinting
Fingerprints database
The fingerprints database we have at our Github repo contains some 450 signatures in a JSON file. Each print is on a single line. If you captured on a live network the JA3 hash d82cbe0b93f2b02d490a14f6bc1d421a you can flag that as PaleMoon Browser 27.4.2
{"desc":"iPad; CPU OS 9_3_5 Safari 601.1", "ja3_hash":"a9aecaa66ad9c6cfe1c361da31768506", "ja3_str":"771,255-49196-49195-49188-49187-49162-49161-49160-49200-49199-49192-49191-49172-49171-49170-157-156-61-60-53-47-10,0-10-11-13-5-18,23-24-25,0" },
{"desc":"PaleMoon Browser; PaleMoon/27.4.2", "ja3_hash":"d82cbe0b93f2b02d490a14f6bc1d421a", "ja3_str":"771,4865-4867-4866-49195-49199-52393-52392-49196-49200-49162-49161-49171-49172-69-136-157-47-65-53-61-132,0-65281-10-11-35-16-5-40-43-13-45,29-23-24-25-256-257-258-259-260,0" },
Analysis of TLS Fingerprints
There are two actionable things you can do with these prints
- Malware prints - These are hard to come by but if you can get a few prints from malware clients. You can flag them quickly. These will likely evade IDS because they use TLS to connect to presumably well known C&C servers with valid certificates etc.
- Anomaly detection : If you can track known prints,then you can build a large Database over a period of time. After that you can send unseen prints into a “Triage state” where a human can look into it.
How the TrisulNSM App works
The TLS Print app is written in LuaJIT and plugs into the TrisulNSM Scripting Engine. The source code for the App is available on the Github trisulnsm/apps repo. Essentially it uses the "TCP Reassembly Handler" Lua script type and parses the Client Hello messages and constructs the JA3 fingerprints and pushes them back into the Trisul streaming pipeline.
The app generates the following pieces of info.
- Metrics : The app generates metrics for each TLS-Print it finds. If the print is a known one, it also updates the label. You can do long term trend analysis to see when each print was seen over the past few months.
- Graph Analytics : When a Print is seen , the edge vertices namely the IP Flow Tuples, and the SNI (Server Name Indication) Extension are added.
- Alerts : Right now we dont have many Malware prints, but when do we have them, the App can generate an alert.
Metrics
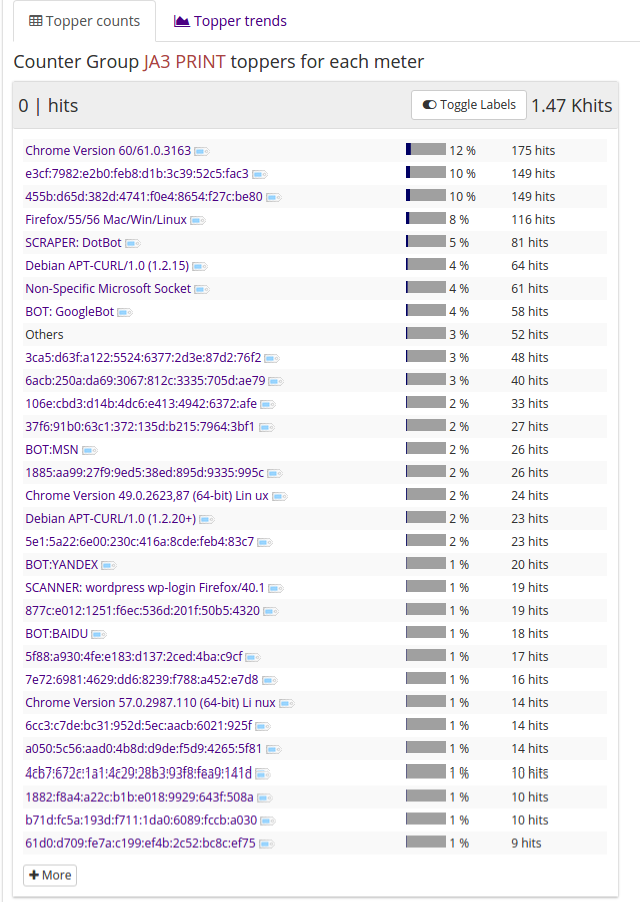
One of the first things you want to check if what kind of coverage does the TLSPrint database have over your network traffic. Go to Retro > Counters > Select the JA3 Print counter group for a view of the top prints shown below.
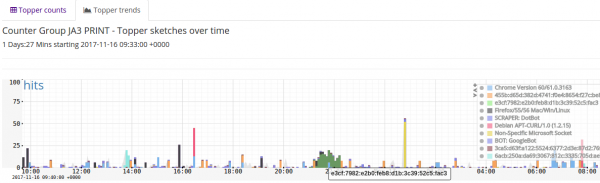
Trends
The above table shows the total number of hits of each TLSPrint over the selected timeframe, you can click on the Trends tab to get the timeseries distribution
Graph Analytics
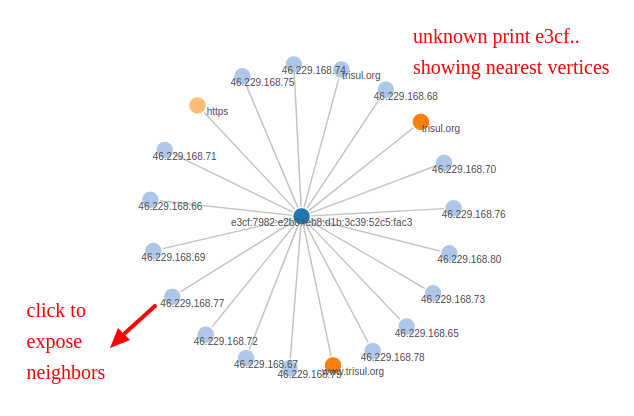
With Trisul EDGE, you can now use streaming graph analytics to explore relationships. For example if you want to see if you can resolve an unknown TLSPrint, click on the small tag to the right of the print and select “View Edges”
This brings up a graph with the selected TLS Print as the root node. See below
You can find all the IPs that are connecting using this TLS-Print. You can then click on any of the IPs and try to reveal its adjacent vertices. You then get the following graph.
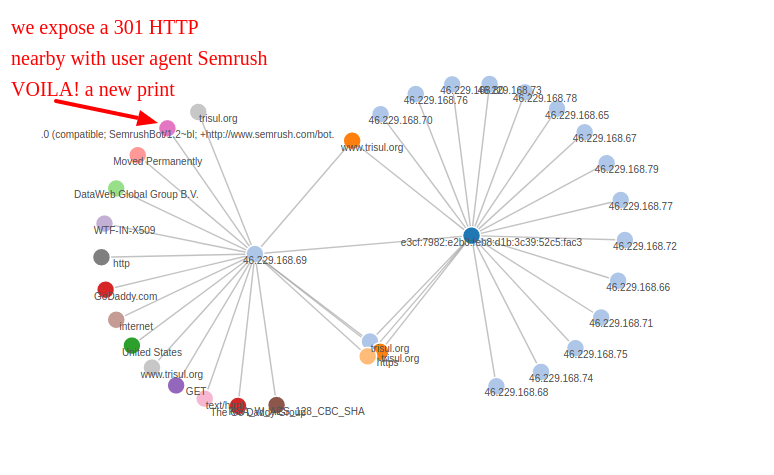
When you reveal adjacent vertices in Trisul EDGE you will see vertices of all types. One of vertex types is User-Agent others are TLS Cert, Country, ASN etc. We are lucky that we found a single User Agent around the same time interval as Semrush - which happens to be a SEO Bot. So there .. this TLS Print can be pegged to SEMRUSH Bot. You can then go to the Key Dashboard and set the label to resolve the previously unknown TLS Print
Programatically resolving TLS Prints
This App dumps all fingerprints along with the parameters used to compute them into a log file. This allows us to programatically resolve unknown fingerprints. We released a TRP Ruby script to programatically resolve TLS Prints using Web Server Access Logs.
We invite you to try this app in your network and let us know how it works. It is free to run .