Table of Contents
How to redirect Netflow to Trisul across network segments using NAT
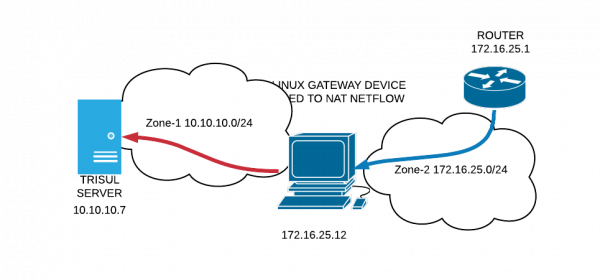
In some customers, Trisul is often deployed on a separate segment from the production routers or routers in the DMZ. These sites often have a gateway device that be be used to access. The routers can reach the gateway to export NETFLOW but cannot reach the Trisul server directly. The picture below shows how the setup is.
This HOWTO explains how to use Linux IPTABLES NAT to solve the issue.
IPTABLES Port based NAT
On the gateway device you just need to run the following commands, say you want to move port 2055 to a particular IP.
Shutdown ufw or disable firewalld
since we are working directly with iptables.
# On Ubuntu ufw disable # On CentOS/RHEL systemctl firewalld stop # Make sure ip forwarding is enabled in kernel echo 1 > /proc/sys/net/ipv4/ip_forward
Then setup the Port NAT
The following commands move port 2055 to the Trisul IP (see the diagram above) .
$ iptables -t nat -A PREROUTING -p udp --dport 2055 -j DNAT --to-destination 10.10.10.17:2055
You should now be seeing Netflow flowing to the Trisul box.
Useful commands
To view NAT rules with counters
iptables -t nat -vL
Reference
Forwarding and NAT with IPTABLES : Redhat https://access.redhat.com/documentation/en-US/Red_Hat_Enterprise_Linux/4/html/Security_Guide/s1-firewall-ipt-fwd.html